Please visit the following link to keep up to date with our blogs.
Wednesday, 12 June 2013
New Blog Page for 7E
As part of our recent rebranding, we now have our blog page hosted within the main 7E website.
Please visit the following link to keep up to date with our blogs.
Please visit the following link to keep up to date with our blogs.
Thursday, 2 May 2013
Innovation Vouchers for Cyber Security
The Technology
Strategy Board within the UK has recently provided access to funding (up
to £5,000) for SMEs, entrepreneurs and early stage start-ups looking to gain
assurance around their ‘Cyber Security’.
Funding IT Security
and assurance activity can be a real barrier to SMEs. When it is placed against
other competing priorities, it often does not win the battle for internal
funding. Nevertheless it remains a key enabler to business success. The UK
Government stepping in to provide help with funding is a really positive step
and a great opportunity for SMEs to overcome the funding barrier.
This blog post takes a
look at the funding on offer and more importantly provides clarity around the
terms used. This will enable organisations to clearly identify those areas they
want to engage with and make best use of this external funding.
First important note:
Closing date for
applications is the 24th July 2013 and is for UK based companies.
Second important note:
Don't be put off or
confused by the term 'Cyber'.
We are actually
talking about information technology and computers.
For more background on
what 'Cyber' and 'Cyber Security' actually means take a look at my last blog
post.
Innovation Vouchers
for Cyber Security
The Innovation
Vouchers can be used to secure specialist services and consulting to help with
the following:
- Businesses looking to protect new
inventions and business processes.
- Businesses looking to ‘cyber audit' their
existing processes.
- Businesses looking to move online and
develop a technology strategy.
- Business start-ups looking to develop an
idea into a working prototype and needing to build cyber security into the
business from the very beginning.
This offers quite a
range of options and many business projects could be aligned to fit and therefore
be eligible for funding, But lets take a look at one specific area
and see what could be done.
Businesses looking
to ‘cyber audit' their existing processes
Lets take 'Cyber' as meaning
information technology and an 'Audit' meaning a systematic review or
assessment. Then a 'Cyber Audit' in this context is more simply put as an audit
of the organisations information security controls.
Audits can be paper based, with an auditor conducting a review of an existing control,
or be delivered as a technical assessment, such as a vulnerability
assessment / penetration test.
Audits are great for
looking at the policy and processes within an organisation, where as a
technical assessment will test that those controls actually deliver the
required or expected level of security. The key here is to choose the most
appropriate engagement for your own requirements.
Why would conducting an audit be a good step to take?
Today our business environment is more complex and interconnected than ever before. Business environments rely on electronic data as their lifeblood and the systems that enable the storage, transport, access and manipulation of this data have become critical. This has resulted in an era where networks and the applications sitting within them have become the very backbone of every organisation, regardless of their size and market sector.
An audit or assessment of an organisation’s current approach to security can be used to identify if adequate information security management is in place to protect the level of information asset being hosted, stored, transmitted or processed.
Just remember to choose a security consultancy that will work in close partnership with you to tailor the solution required and not just sell you a 'Cyber Product'.
A good engagement will leave you with a clear understanding of areas for improvement, the potential impact to you and more importantly what can be done to address these.
A bad engagement will most likely leave you swimming in a sea of FUD (Fear, Uncertainty and Doubt) and the frequency of the word 'Cyber' is likely to be proportional to the amount of proprietary solutions that the vendor sells to fix the issues they find.
Conclusion
Costs can be a
significant barrier for SMEs when it comes to security and the use of jargon
can get in the way of our understanding of what can be done and why it is
important.
However, even small organisations need to be aware of their exposure to security. So, with the use of funding and approaching it from a knowledgeable position you can drive an engagement that will enable your organisation to gain an understanding of the security risks you carry and how to start addressing them in a risk based manner.
Tuesday, 30 April 2013
What is Cyber Security?
A question that I am often asked is "What is Cyber Security?"
Cybersecurity or Cyber Security is a widely used term and one that most people will now have heard of. Many will need to understand the term if they are tasked with protecting information systems. Cyber Security as a term can be found in news articles from the
mid-late 1990s when the US Government started to understand how interconnected their systems had become and therefore potentially at risk of compromise.
However, there are many definitions that use the word 'Cyber' and I find that they are often confusing, for example:
"Cyber security involves protecting information and systems from major cyber threats, such as cyber terrorism, cyber warfare, and cyber espionage."
Great, so Cyber Security is protecting you from Cyber <insert problem here>? Is that it, or am I missing something?
Unfortunately it is often used as part of a sales pitch and can often be misused to create a state of fear, uncertainty and doubt (FUD) aimed at generating interest in a product or service. You will often see terms such as Cyber Crime, Cyber Strategy Cyber Security Awareness and Cyber Threat.
Lets deconstruct this further.
So, what have we got so far, well Cyber is essentially a buzz word used widely within the Information Security world to capture all 'evil' activity conducted over the Internet or interconnected networks and systems.
Time to define Cyber.
What do I understand the term Cyber to mean? Well lets get away from the hype and go back to basics. To do this, we can take a look and see how the term cyber is defined within the Oxford Dictionary:
If you are looking for a more formal definition of Cyber Security then the Centre for the Protection of National Infrastructure (CPNI) has a great example that is easy to follow and avoids over use of the word Cyber:
Cybersecurity or Cyber Security is a widely used term and one that most people will now have heard of. Many will need to understand the term if they are tasked with protecting information systems. Cyber Security as a term can be found in news articles from the
mid-late 1990s when the US Government started to understand how interconnected their systems had become and therefore potentially at risk of compromise.
However, there are many definitions that use the word 'Cyber' and I find that they are often confusing, for example:
"Cyber security involves protecting information and systems from major cyber threats, such as cyber terrorism, cyber warfare, and cyber espionage."
Great, so Cyber Security is protecting you from Cyber <insert problem here>? Is that it, or am I missing something?
Unfortunately it is often used as part of a sales pitch and can often be misused to create a state of fear, uncertainty and doubt (FUD) aimed at generating interest in a product or service. You will often see terms such as Cyber Crime, Cyber Strategy Cyber Security Awareness and Cyber Threat.
Lets deconstruct this further.
So, what have we got so far, well Cyber is essentially a buzz word used widely within the Information Security world to capture all 'evil' activity conducted over the Internet or interconnected networks and systems.
Time to define Cyber.
What do I understand the term Cyber to mean? Well lets get away from the hype and go back to basics. To do this, we can take a look and see how the term cyber is defined within the Oxford Dictionary:
"cyber
Pronunciation: /ˈsʌɪbə/
Definition
of cyber
adjective
·
relating to or characteristic of the
culture of computers, information technology, and virtual reality:the cyber
age"
Therefore, Cyber can be defined as the use of information technology and computers. I think that this is a straight forward and an understandable way of looking at it. It is therefore, no longer a 'scary' word used to frighten us.
Time to define Cyber Security.
So, looking at how to define Cyber Security, if we build upon our understanding of Cyber, we can see that what we are now talking about is the security of information technology and computers. Which is basically good old fashioned information security controls.
For me, Cyber Security should be replaced with:
"Information Security"
Doesn't that sound so much clearer!
If you are looking for a more formal definition of Cyber Security then the Centre for the Protection of National Infrastructure (CPNI) has a great example that is easy to follow and avoids over use of the word Cyber:
"Almost every business relies on the confidentiality, integrity and availability of its data. Protecting information, whether it is held electronically or by other means, should be at the heart of the organisation’s security planning. The key questions to keep under constant review are:
- Who would want access to our information and how could they acquire it?
- How could they benefit from its use?
- Can they sell it, amend it or even prevent staff or customers from accessing it?
- How damaging would the loss of data be? What would be the effect on its operations?"
Friday, 1 February 2013
Resilient Information Security
I recently had the opportunity to speak at the Edinburgh Symposium on Information Security: Governance, Sharing and Risk in a Digital Age on the topic of resilient information security. Testing for an organisation's resilience to an Information Security incident is an area of research that I have created and developed.
I have worked within the technical security market for the last thirteen years, where I have gained a wealth of experience through the delivery of technical security tests for both private and public sector organisations and I have dealt with many large scale and high profile security incidents. During this time I have realised that we, as an industry have only put half of the puzzle in place in terms of our approach to assurance and we should be doing more.
Resilient Information Security Assurance is an area that I have developed to fill this gap.
Introduction
For many organisations, their approach to Information Security results in a fortress mentality that focusses on the implementation of defences and preventing an attack. This approach has directly influenced compliance and assurance approaches, such as vulnerability scanning and penetration testing. It is often acknowledged however, that we cannot build sufficient defences to be 100% secure while allowing our organisations to effectively carry out their business, and as such, for many this siege based approach and associated assurance methodology is no longer acceptable.
When presenting on the issue of Information Security, one of the main conclusions that I keep returning to can be summed up by the following,
We should approach this problem from the point of view of business resiliency, which captures the ability for an organisation to be robust to attack and to be able to detect, react and recover from any incident.
So, given this, why do we still silo our assurance activity?
We need a new approach to security assurance that not only tests for an organisation's defensive posture, but also assesses their resilience to attack. It's time for 'Resilient Security Testing'.
Resilient Security Testing
How can we achieve this? At a high-level by changing our assurance activity from an often narrow, isolated focus to a more holistic approach that assesses an organisation's position against the following four core areas:
This holistic view will enable organisations to test that they have in place a system that is resilient to an attack, thus building resilience into the management of Information Security. Doing so will enable organisations to deliver the right balance between security and operational, business, and regulatory requirements, while enabling them to gain the assurance that such systems actually deliver the required results.
While I have developed this new approach, 7 Elements are leading its development. We will follow this blog post with a paper dedicated to further detail on how each of these areas can be tested and the outcomes we would look for.
OSSRAM
As part of our commitment to support the wider Information Security community, we have also established and will provide ongoing support for OSSRAM, the Open Source Security Resilience Assurance Methodology. This will provide a platform for individuals and organisations to work together in the development and delivery of a robust and open source assurance methodology.
I have worked within the technical security market for the last thirteen years, where I have gained a wealth of experience through the delivery of technical security tests for both private and public sector organisations and I have dealt with many large scale and high profile security incidents. During this time I have realised that we, as an industry have only put half of the puzzle in place in terms of our approach to assurance and we should be doing more.
Resilient Information Security Assurance is an area that I have developed to fill this gap.
Introduction
For many organisations, their approach to Information Security results in a fortress mentality that focusses on the implementation of defences and preventing an attack. This approach has directly influenced compliance and assurance approaches, such as vulnerability scanning and penetration testing. It is often acknowledged however, that we cannot build sufficient defences to be 100% secure while allowing our organisations to effectively carry out their business, and as such, for many this siege based approach and associated assurance methodology is no longer acceptable.
When presenting on the issue of Information Security, one of the main conclusions that I keep returning to can be summed up by the following,
We should approach this problem from the point of view of business resiliency, which captures the ability for an organisation to be robust to attack and to be able to detect, react and recover from any incident.
So, given this, why do we still silo our assurance activity?
We need a new approach to security assurance that not only tests for an organisation's defensive posture, but also assesses their resilience to attack. It's time for 'Resilient Security Testing'.
Resilient Security Testing
How can we achieve this? At a high-level by changing our assurance activity from an often narrow, isolated focus to a more holistic approach that assesses an organisation's position against the following four core areas:
This holistic view will enable organisations to test that they have in place a system that is resilient to an attack, thus building resilience into the management of Information Security. Doing so will enable organisations to deliver the right balance between security and operational, business, and regulatory requirements, while enabling them to gain the assurance that such systems actually deliver the required results.
OSSRAM
As part of our commitment to support the wider Information Security community, we have also established and will provide ongoing support for OSSRAM, the Open Source Security Resilience Assurance Methodology. This will provide a platform for individuals and organisations to work together in the development and delivery of a robust and open source assurance methodology.
Tuesday, 29 January 2013
Cell Injection
[Cell Injection] Attacking the end user through the application.
[Introduction]
At 7 Elements our approach to application security testing blends the identification of technical exposure with business logic flaws, which could lead to a breach in security. By taking this approach, and by understanding the business context and envisaged use, it is possible to provide a deeper level of assurance. We have used this approach to identify a novel attack that we have called, cell injection.
[What is Cell Injection?]
Cell injection occurs where a user is able to inject valid spreadsheet function calls or valid delimited values into a spread sheet via a web front end that results in unintended consequences. A number of attacks exist, from simple data pollution to more harmful calls to external sources.
[Basic injection technique]
At a simple level we can look to inject values that we can expect to be interpreted as valid Comma-Separated Values (CSV). For a widely used format, there is still no formal specification, which according to RFC4180 "allows for a wide variety of interpretations of CSV files". As such we should look to inject common values such as semicolon, comma or tab but also other values such as the ASCII characters " | ", "+" and "^".
If these values are interpreted by the spreadsheet, then you can expect data pollution to occur . This happens by shifting cells from their expected location. The following example shows the "|" character being used to insert additional cells within a spreadsheet. This was done by inserting four "|" values within the 'Amount' field, which results in the shifting of the values expected within D4 and E4 to appear in H4 and I4:
Where it is possible to insert the "=" sign, we can then attempt to use function calls within the spreadsheet.
Microsoft list all possible functions, however, the one we are interested in for the purpose of attack is the HYPERLINK function. Which has the following syntax:
HYPERLINK(link_location,friendly_name)
What can you do with it? Firstly, we need to change the injected string to point to an external site under our control. For this example we will use our web site by submitting the following string:
If the friendly_name specified is created within the spread sheet then we have successfully injected our data:
Within Microsoft Excel, a user clicking on this link will not be prompted for any confirmation that they are about to visit an external link. A single click will be enough to launch a browser and load the destination address. Using this approach, an attacker could configure the url to point to a malicious site containing browser based malware and attempt to compromise the client browser and gain access to the underlying operating system.
[Advanced Injection]
The basic HYPERLINK attack requires that you can inject double quotation marks around the link and friendly_name values. As this can be a commonly filtered out input, the basic attack may fail. To bypass this restriction, it is possible to use a more advanced technique to generate a valid HYPERLINK function. This approach uses calls to other cells within the spread sheet and therefore negates the requirement to supply double quotes. To use this approach you will need to set one cell as a “friendly_name” and a second cell as the "link_location”. Lastly you will then need to inject the the HYPERLINK function, that references the locations of these fields. The following string shows such an attack:
As part of this Proof of Concept, we have hard-coded the cell values E4 and F4, but we believe it should be possible to dynamically create these using the ROW() and COLUMN() functions. Using this approach we can then create the 'Click Here' cell without the need for double quotes:
During our tests we have also identified other attack vectors, such as updating fields or cell value lookup functions, where we do not have direct access to the content from the web application. This could be used to overwrite data for our own gain or populate a cell that is then later used to echo out data to a client with a value from a normally hidden cell.
[Mitigation]
As this attack is focused on the end user of the spreadsheet, mitigation is best placed at the point the data is first input. As such we would recommend that user input is validated based upon what is required. The best method of doing this is via 'white-listing'. Where possible, all characters that have a valid meaning within the destination spread sheet should be removed from your white-list of valid characters. We would also recommend that where possible you do not permit the equals sign as the first character in a field.
[Setting the scene]
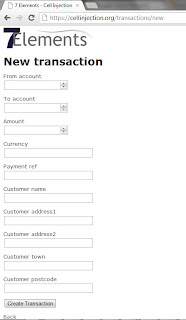
To illustrate this attack and to provide context we will use a scenario that we often come across during our engagements and is based on the use of third party provisioned services to deliver transactional functionality. With this type of service we often find that the back end data management and record retention is achieved by the use of spread sheets. To help provide a working example, we have developed a dummy transactional website. This site has two main functions, the end user facing application and an admin section. Users access the application over the internet to transfer funds electronically. The end organisation utilises the admin functionality to manage the site and via the application they can view transactions. They are also provided with the ability to download transactional data for internal processing and data retention. At a high level it would look like this:
[Attack Surface]
The main input fields that an attacker can interact with are as follows:
The application has been designed to provide defence against the OWASP Top 10. Specifically, the application has been coded to defend against common input validation attacks such as SQL Injection and Cross Site Scripting, as well as correctly validating all output that is displayed within the application.
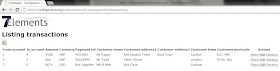
Given this scenario, the attack option will be limited to attacking the 'Back Office' component of this application. Robust security measures, as already discussed, have mitigated attacks against end users of the application, and direct attacks against the application and database have been mitigated. On further inspection, and through a manual testing approach that looks at the end to end business process involved, it would be noted that the 'Back Office' function of this application relies on the download and use of spread sheet data:
The data is lifted directly from the database and on download results in the spread sheet opening on the 'Back Office' computer screen:
Let's now use our cell injection to compromise the integrity of the data stored within the spreadsheet and gain remote access to the 'Back Office' computer.
[Exploit]
The following video shows how an attacker can use cell injection via the front client facing application to compromise an internal host. The attack requires the end user to place trust in the data, but then who doesn't trust content that they have decided to download?
Blogger video is a little limited, so for those who want to see all the detail, we have hosted the video here.
[Conclusion]
By taking the time to understand how data would be input into the system, and more importantly where the data is then output to an end user, we were able to develop a specific attack approach to directly target end users of the data and gain unauthorised access to systems and data.
In this example, correct encoding of user supplied data in the context of its use had not been fully implemented and without this level of testing, would have appeared to be protected against input / output validation based attacks. This could lead to a false sense of security. Further to this, being able to attack internal hosts directly changes the assumed threat surface and therefore would raise issues around browser patch management and the lack of egress filtering in place.
As we have seen from this blog, testing should be more than just the OWASP Top 10. We need to think about the overall context of the application, the business logic in use and ultimately where and how our input is used and how it manifests as output. This provides a further example of the need to take a layered approach to security and accept that you can not achieve 100%. This highlights the need to implement a resilient approach, building upon a robust defensive posture, that takes into account the need to be able to detect, react and recover from a breach.
[Introduction]
At 7 Elements our approach to application security testing blends the identification of technical exposure with business logic flaws, which could lead to a breach in security. By taking this approach, and by understanding the business context and envisaged use, it is possible to provide a deeper level of assurance. We have used this approach to identify a novel attack that we have called, cell injection.
[What is Cell Injection?]
Cell injection occurs where a user is able to inject valid spreadsheet function calls or valid delimited values into a spread sheet via a web front end that results in unintended consequences. A number of attacks exist, from simple data pollution to more harmful calls to external sources.
[Basic injection technique]
At a simple level we can look to inject values that we can expect to be interpreted as valid Comma-Separated Values (CSV). For a widely used format, there is still no formal specification, which according to RFC4180 "allows for a wide variety of interpretations of CSV files". As such we should look to inject common values such as semicolon, comma or tab but also other values such as the ASCII characters " | ", "+" and "^".
If these values are interpreted by the spreadsheet, then you can expect data pollution to occur . This happens by shifting cells from their expected location. The following example shows the "|" character being used to insert additional cells within a spreadsheet. This was done by inserting four "|" values within the 'Amount' field, which results in the shifting of the values expected within D4 and E4 to appear in H4 and I4:
Where it is possible to insert the "=" sign, we can then attempt to use function calls within the spreadsheet.
Microsoft list all possible functions, however, the one we are interested in for the purpose of attack is the HYPERLINK function. Which has the following syntax:
HYPERLINK(link_location,friendly_name)
What can you do with it? Firstly, we need to change the injected string to point to an external site under our control. For this example we will use our web site by submitting the following string:
If the friendly_name specified is created within the spread sheet then we have successfully injected our data:
Within Microsoft Excel, a user clicking on this link will not be prompted for any confirmation that they are about to visit an external link. A single click will be enough to launch a browser and load the destination address. Using this approach, an attacker could configure the url to point to a malicious site containing browser based malware and attempt to compromise the client browser and gain access to the underlying operating system.
[Advanced Injection]
The basic HYPERLINK attack requires that you can inject double quotation marks around the link and friendly_name values. As this can be a commonly filtered out input, the basic attack may fail. To bypass this restriction, it is possible to use a more advanced technique to generate a valid HYPERLINK function. This approach uses calls to other cells within the spread sheet and therefore negates the requirement to supply double quotes. To use this approach you will need to set one cell as a “friendly_name” and a second cell as the "link_location”. Lastly you will then need to inject the the HYPERLINK function, that references the locations of these fields. The following string shows such an attack:
As part of this Proof of Concept, we have hard-coded the cell values E4 and F4, but we believe it should be possible to dynamically create these using the ROW() and COLUMN() functions. Using this approach we can then create the 'Click Here' cell without the need for double quotes:
During our tests we have also identified other attack vectors, such as updating fields or cell value lookup functions, where we do not have direct access to the content from the web application. This could be used to overwrite data for our own gain or populate a cell that is then later used to echo out data to a client with a value from a normally hidden cell.
[Mitigation]
As this attack is focused on the end user of the spreadsheet, mitigation is best placed at the point the data is first input. As such we would recommend that user input is validated based upon what is required. The best method of doing this is via 'white-listing'. Where possible, all characters that have a valid meaning within the destination spread sheet should be removed from your white-list of valid characters. We would also recommend that where possible you do not permit the equals sign as the first character in a field.
Time for a working example and exploit:
[Setting the scene]
To illustrate this attack and to provide context we will use a scenario that we often come across during our engagements and is based on the use of third party provisioned services to deliver transactional functionality. With this type of service we often find that the back end data management and record retention is achieved by the use of spread sheets. To help provide a working example, we have developed a dummy transactional website. This site has two main functions, the end user facing application and an admin section. Users access the application over the internet to transfer funds electronically. The end organisation utilises the admin functionality to manage the site and via the application they can view transactions. They are also provided with the ability to download transactional data for internal processing and data retention. At a high level it would look like this:
[Attack Surface]
The main input fields that an attacker can interact with are as follows:
The application has been designed to provide defence against the OWASP Top 10. Specifically, the application has been coded to defend against common input validation attacks such as SQL Injection and Cross Site Scripting, as well as correctly validating all output that is displayed within the application.
Given this scenario, the attack option will be limited to attacking the 'Back Office' component of this application. Robust security measures, as already discussed, have mitigated attacks against end users of the application, and direct attacks against the application and database have been mitigated. On further inspection, and through a manual testing approach that looks at the end to end business process involved, it would be noted that the 'Back Office' function of this application relies on the download and use of spread sheet data:
The data is lifted directly from the database and on download results in the spread sheet opening on the 'Back Office' computer screen:
[Exploit]
The following video shows how an attacker can use cell injection via the front client facing application to compromise an internal host. The attack requires the end user to place trust in the data, but then who doesn't trust content that they have decided to download?
[Conclusion]
By taking the time to understand how data would be input into the system, and more importantly where the data is then output to an end user, we were able to develop a specific attack approach to directly target end users of the data and gain unauthorised access to systems and data.
In this example, correct encoding of user supplied data in the context of its use had not been fully implemented and without this level of testing, would have appeared to be protected against input / output validation based attacks. This could lead to a false sense of security. Further to this, being able to attack internal hosts directly changes the assumed threat surface and therefore would raise issues around browser patch management and the lack of egress filtering in place.
As we have seen from this blog, testing should be more than just the OWASP Top 10. We need to think about the overall context of the application, the business logic in use and ultimately where and how our input is used and how it manifests as output. This provides a further example of the need to take a layered approach to security and accept that you can not achieve 100%. This highlights the need to implement a resilient approach, building upon a robust defensive posture, that takes into account the need to be able to detect, react and recover from a breach.
Monday, 21 January 2013
Vacancy: Security Tester
Wednesday, 16 January 2013
Symposium on Information Security Part Two
Following on from the morning overview, Marek now takes a look at the afternoon sessions.
Alex Stobart from Mydex-
Citizen-centred personal Data stores. Mydex has been chosen to be one of 9
Digital Public Services. Mydex will provide Identity Assurance that empowers
the individuals to manage their personal data and acquire proof of claim and
verification about any aspect of their life and identity. Citizens can create a
Secure Personal Data Unit, which allows them to collect information and within
the control layer decide with which party it will share certain types of information.
The difference with Mydex is that individuals self drive the personal data unit
rather than it be controlled by an organisation.
How does information
security impact innovation and collaboration? This topic was presented by Richard
Higgs from Brightsolid company, The presenter used real client experiences,
describing how the company could manage the innovative collaborative space
within the cloud and still assure a level of security. Nowadays a lot of
companies are moving most of their business or even parts to the cloud and are
facing issues related to how co-workers collaborate on new projects. Moving infrastructure
to the cloud companies need to increase security awareness for their employees
as well. Brightsolid showed how their company could achieve that.
David Stubley presented Resilient
Information Security: A New Approach to Assurance. Many organisations
nowadays see computer networks and applications as the backbone for their
business and as a result focus on the implementation of defences and preventing
attacks. This approach has directly influenced compliance and assurance
approaches, such as vulnerability scanning and penetration testing. We cannot
achieve 100% security and allow the business to run flawlessly. This approach
is becoming unacceptable for many businesses. David presented a new approach to
assurance that would not only test the defences of an organisation but also
test it resilience to attack.
The example showed on the presentation was a Java zero-day, which was publicly announced just a day before. At the moment the zero-day is being publicly discussed and is marked as High-risk by Oracle. Countermeasures are available. The question is how long this zero-day was available? This new approach to assurance would allow implementing the resilience into the management of Information Security and will enable organisations to deliver a balance between security and operational requirements.
The example showed on the presentation was a Java zero-day, which was publicly announced just a day before. At the moment the zero-day is being publicly discussed and is marked as High-risk by Oracle. Countermeasures are available. The question is how long this zero-day was available? This new approach to assurance would allow implementing the resilience into the management of Information Security and will enable organisations to deliver a balance between security and operational requirements.
As a result of this idea the Open Source Security Resilience
Assurance Methodology (OSSRAM) was created. OSSRAM is an open source community
looking at how to define this new approach to resiliency testing and assurance.
The community is welcome to access the website and express their opinions.
Part of the symposium was the announcement of the Cyber Security
Student of the year 2013, the first three finalists were: Charley Celice;
Gordon Grey and Hector Grebbell, congratulations to all participants and
winners.
Gordon Mullin from Memex presented Big Data, Analytics and Information Security. Gordon outlined the
issues related to Big Data, how a company could take advantage of it, how and
what models to use for sharing the amount of data and how to effectively
implement the enforcement solutions using this data. Some of the examples
showed how Big Data analysis could help the police effectively reduce violence
during events. The Memex solution allows analysis of Big Data and provides
relevant information to the right people.
Paul Thomas and Phil Strading from Microsoft presented Human Trust in Digital Life. This talk
returned back to the e-Health topic and the potential role of e-Health to meet
the higher demand of health and care service. These services, which are
controlled by the public sector, are moving towards the sector consisting of family,
individuals, and the commercial sector. This talk outlined the new
technologies, processes and governance which need to take place in order to
provide trust over the internet between individuals, third sector and statutory
services. The program will help in UK to deliver a service for assisted living
and manag the care system.
The last speaker was Don Smith from Dell SecureWorks who
presented Governance, don't forget to
lock your doors… Don outlined the problems that lie within the industry using
live scenarios. One of their clients came under attack for some time. It was an
un-known type of the attack with focus on a Java. The Java exploit was out for several
months before it has been disclosed. As the exploit became disclosed it also
became available to the public. There was still a time gap before the relevant
companies released the patch to eliminate it. The other question raised is when
the patch is available how long does it takes for organisations to deploy this
patch to their environment? This scenario showed how vulnerable our data can
be. They could be accessed maliciously using zero-day attacks and even when
they are disclosed and patches made available there are still many companies that
would be vulnerable to it.
Don as well as David before, mentioned the new Java zero-day
disclosed by Alien Vault on 10 January.
David raised the question of how long was this zero-day wild on the Internet
before the relevant organisations noticed?